- 1-10課
- 11-20課
- 31-40課
- 41-50課
- 51-60課
- 61-70課
- 71-80課
第十六課:紅藍對抗?jié)B透測試1
專注APT攻擊與防御
https://micropoor.blogspot.com/
前言:
在團體滲透測試的項目中,如紅藍對抗,團隊滲透測試比賽等,最重要的是過程與結(jié)果實時共享于團隊,例如:A同學nmap目標站,B同學也nmap目標站,這在對抗比賽中是極其浪費時間也是非常容易引起防火墻,日志服務器或其他設備的警覺。所以打算寫一系列關于未來團隊滲透的對抗。爭取做到過程與結(jié)果,團隊實時共享。把曾經(jīng)的團隊作戰(zhàn)經(jīng)驗形成一個適應對抗,比賽等的參考。
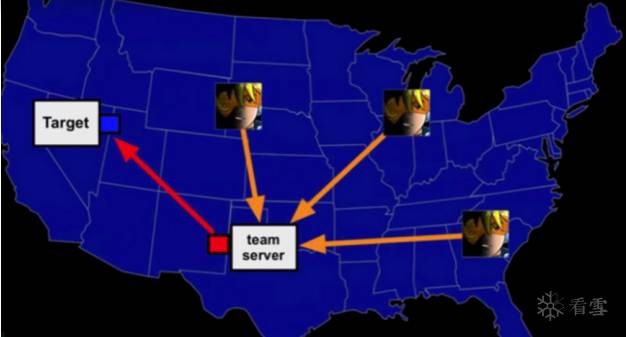
BloodHound簡介:
BloodHound是2016年出現(xiàn)大家的視線中,它是一個分析和解讀AD中權限關系的一個工具。對于攻擊者來說,能快速的獲取到域中的線索以便進行下一步攻擊,而對于防御者來說,可以更快速的得知攻擊者可能采取的攻擊途徑以及域中的可突破的途徑。
項目地址:
https://github.com/BloodHoundAD/BloodHound
Debian上安裝:
root@John:~# apt-get install git wget curl
root@John:~# wget -O - https://debian.neo4j.org/neotechnology.gpg.key | sudo
apt-key add
root@John:~# echo 'deb http://debian.neo4j.org/repo stable/' | sudo tee
/etc/apt/sources.list.d/neo4j.list
root@John:~# apt-get install openjdk-8-jdk openjdk-8-jre
root@John:~# apt-get install neo4j
root@John:~# echo "dbms.active_database=graph.db" >> /etc/neo4j/neo4j.conf
root@John:~# echo "dbms.connector.http.address=0.0.0.0:7474" >>
/etc/neo4j/neo4j.conf
root@John:~# echo "dbms.connector.bolt.address=0.0.0.0:7687" >>
/etc/neo4j/neo4j.conf
root@John:~# tail /etc/neo4j/neo4j.conf
# Name of the service
dbms.windows_service_name=neo4j
#********************************************************************
# Other Neo4j system properties
#********************************************************************
dbms.jvm.additional=-Dunsupported.dbms.udc.source=tarball
dbms.active_database=graph.db
dbms.connector.http.address=0.0.0.0:7474
dbms.connector.bolt.address=0.0.0.0:7687
root@John:~j# update-java-alternatives -l
java-1.8.0-openjdk-amd64 1081 /usr/lib/jvm/java-1.8.0-openjdk-amd64
root@John:~j# update-java-alternatives -s java-1.8.0-openjdk-amd64
下載地址:https://neo4j.com/download/
root@John:~/Downloads# tar zxvf neo4j-community-3.3.0-unix.tar.gz
root@John:~/Downloads/neo4j-community-3.3.0/bin# ./neo4j start
Active database: graph.db
Directories in use:
home: /root/Downloads/neo4j-community-3.3.0
config: /root/Downloads/neo4j-community-3.3.0/conf
logs: /root/Downloads/neo4j-community-3.3.0/logs
plugins: /root/Downloads/neo4j-community-3.3.0/plugins
import: /root/Downloads/neo4j-community-3.3.0/import
data: /root/Downloads/neo4j-community-3.3.0/data
certificates: /root/Downloads/neo4j-community-3.3.0/certificates
run: /root/Downloads/neo4j-community-3.3.0/run
Starting Neo4j.
WARNING: Max 1024 open files allowed, minimum of 40000 recommended. See the
Neo4j manual.
Started neo4j (pid 4286). It is available at http://localhost:7474/
There may be a short delay until the server is ready.
See /root/Downloads/neo4j-community-3.3.0/logs/neo4j.log for current status.
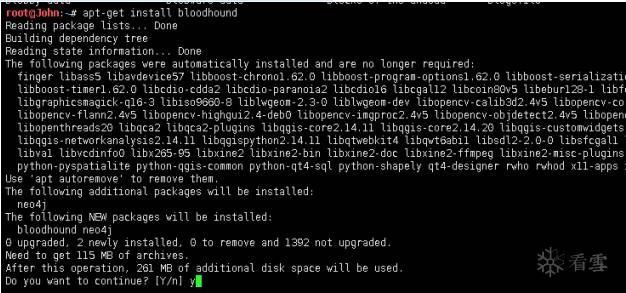
root@John:~# apt-get install bloodhound
root@John:~/Downloads/neo4j-community-3.3.0/bin# nmap 127.0.0.1 -p 7474
Starting Nmap 7.40 ( https://nmap.org ) at 2017-12-02 11:16 EST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00011s latency).
PORT STATE SERVICE
7474/tcp open neo4j
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds

Micropoor
?
問答
其他問答

暫無記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開":"未公開"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無記錄
作業(yè)

暫無記錄

